 Sega Hacked:1.3 Million Accounts Compromised
Sega Hacked:1.3 Million Accounts Compromised
Information belonging to 1.3 million customers was stolen in a recent cyber attack against Japanese game developer Sega.
The attackers stole email addresses, encrypted passwords, and birth dates for some Sega Pass customers; however, payment and credit card information for those accounts was not compromised. For the time being Sega Pass has been shut down until security can be strengthened.The following letter posted on Playstation Lifestyle went out to Sega Pass customers who may have potentially been affected by the attack:
Dear ___,
As you may be aware, the SEGA Pass system has been offline since yesterday, Thursday 16 June.
Over the last 24 hours we have identified that unauthorised entry was gained to our SEGA Pass database.
We immediately took the appropriate action to protect our consumers’ data and isolate the location of the breach. We have launched an investigation into the extent of the breach of our public systems.
We have identified that a subset of SEGA Pass members emails addresses, dates of birth and encrypted passwords were obtained. To stress, none of the passwords obtained were stored in plain text.
Please note that no personal payment information was stored by SEGA as we use external payment providers, meaning your payment details were not at risk from this intrusion.
If you use the same login information for other websites and/or services as you do for SEGA Pass, you should change that information immediately.
We have also reset your password and all access to SEGA Pass has been temporarily suspended.
Additionally we recommend you please take extra caution if you should receive suspicious emails that ask for personal or sensitive information.
Therefore please do not attempt to login to SEGA Pass at present, we will communicate when the service becomes available.
We sincerely apologise for this incident and regret any inconvenience caused.
We are contacting all our members with these recommendations.
If you have any further questions please contact SEGA customer support on csescalations@sega.com
In an interesting show of support, hacker group LulzSec has offered to help Sega take down whatever party was responsible for the attack.
Were any of you affected by the attack? What do you think about the rash of attacks hitting game companies in recent months?
LulzSec At It Again! Releases 62,000+ E-mails, Passwords
Lulz Security, a griefer group largely credited (blamed?) for its unwavering Sony attacks, was back at it again this week. Following its hacks of the U.S. Senate website, the group has claimed responsibility for two high-profile incidents: the packet-flooding (and crash) of the CIA’s website and an exploit that leaked a monster list of private e-mail addresses and passwords into the wild.
LulzSec announced both hacks via its Twitter account. Criminally, the CIA attack is big — huge, in fact — at least on a national security level. But it’s the group’s second exploit that could be even more upsetting for the public: Confidential data was plucked from Bethesda Software, including server admin configurations, admin staff and blog user hashes, server logs, and mappings of Arkane, Bethblog, Brink codes, Brink signups, IDSoftware, Rage, and others.
End result? The group compromised more than 62,000 email addresses and passwords.
The last time the group performed a digital “smash and grab” of e-mail addresses and passwords, they took 26,000 of them from porn sites. This time, LulzSec isn’t saying if it pinpointed certain sources or how the data was collected from the public. But it did post the entire list via a Mediafire download link that was widely covered this week — which is sad, because the link got yanked, leaving people without a way to check if they were victimized.
LulzSec wound up posting the list in its entirety on its own website, so if you’re worried about your info, you can find it here and conduct a simple page search to alleviate your concerns. No doubt malicious people will be hitting this hard, so if you’re on the list, it should go without saying that you’ll want to change your password. You may even want to ditch this account, if you can, and choose a new e-mail address.
In the end, the more innocuous hack of the two — crashing the CIA’s site — could be the very thing that brings the fury down on them. (The intelligence agency doesn’t take kindly to people messing with them.) Some people would be thrilled to see the group get taken down, while others support them like fans devotedly following their favorite action heros.
Where do you stand? Are the LulzSec hackers — and for that matter, Anonymous and its own multi-country cells of cyber attackers — the white-hat digital activists that their supporters make them out to be, or do you consider these groups to be online terrorists leaving behind an unconscionable trail of innocent victims?
[via ZDNet]
UPDATE: Questions have been surfacing about whether LulzSec is attacking Anonymous. These stem from claims that the former made about infecting /b/ (short for http://boards.4chan.org/b/. It’s a subsection of 4chan, which is used by some Anonymous hackers). On Wednesday, 4Chan.org was down for a little while, leading people to think that LulzSec was going after Anonymous, but the group has come out to deny this. For more info, hit up this link.
CIA Website Allegedly Attacked By LulzSec Hackers
The Huffington Post Bianca Bosker First Posted: 06/15/11 06:10 PM ET Updated: 06/15/11
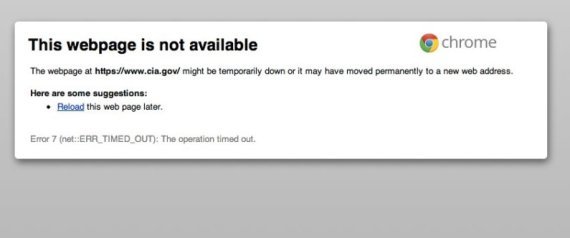
The homepage of the Central Intelligence Agency, http://cia.gov/, appeared to have been suffered an attack from a hacker group on Wednesday evening.
The CIA site would not load properly and website DownForEveryoneOrJustMe.com confirmed that the site was down. However, ReadWriteWeb's Curt Hopkins, who notes that he lives across the country from CIA headquarters, said the website appeared "normal."
LulzSec, a hacker group that has attacked the Senate website twice in a week, claimed responsibility for the outage in a tweet.
"Tango down - cia.gov - for the lulz," @LulzSec tweeted around 5:48PM ET.
LulzSec recently announced that it had established a hotline at which it would be accepting requests for new sites and services to target. LulzSec has claimed responsibility for attacks on Sony, gaming company Bethesda, PBS.org, as well as gaming sites Minecraft and League of Legends. The group's motto reads, "Laughing at your security since 2011."
LulzSec has not added the CIA to its list of "releases"--documents containing information taken during its cyber attacks--on its website and it's possible that the group may have brought down the website, though not taken sensitive data from the agency.
Still, the attack is likely to be taken as a serious affront to the CIA, given its national security responsibilities.
"I think the guys at LulzSec may have just made the biggest mistake of their lives," security expert Graham Cluley told the Huffington Post in an email. "The CIA aren't going to like having their nose bloodied like this."
All Things D writes of the alleged denial of service attack, "The site is for all intents and purposes the public face of the agency, so it’s not likely that any classified information is being taken or any sensitive communications disrupted, but attacking government Web sites is a federal crime under the Computer Fraud and Abuse Act, and probably some other laws I’m not thinking of."
The group said of its previous attack on Senate computers, "We don't like the US government very much. Their boats are weak, their lulz are low, and their sites aren't very secure. In an attempt to help them fix their issues, we've decided to donate additional lulz in the form of owning them some more!"
The CIA was not immediately available for comment.
